Steps to Protecting Your Company Against Phishing Attacks
We discuss key actions that will enable you to protect your company against phishing attacks in China and across Asia.
Phishing email attacks has become a major cause of data breaches and is one of the most dangerous security threats to companies. A white paper published by the Security of China Corporate Mailbox stated that 34.43 billion phishing mails were received in 2019, showing an increase of 68.5 percent compared to 2018. In another report, by the US Federal Bureau of Investigation (FBI), it was stated that between June 2016 and July 2019, companies across the United States and 177 other countries suffered over US$26 billion worth of losses.
During COVID-19, many companies have turned to remote work arrangements, and now more than ever, rely heavily on email communication. As the opportunities for attacks grow larger, traditional phishing emails (sent to a large group of random recipients) have given way to more sophisticated attacks, such as spear phishing, or whaling specific targets.
With 30 percent of phishing emails able to bypass default security measures and another 30 percent of them being opened by target users, what can you do to keep your company protected? In this article, we will introduce the basic characteristics of phishing emails and the risks they pose as well as provide some effective solutions to secure against phishing emails and reduce the related risks to companies.
What is phishing mail and what kind of risks does it pose?
Phishing is a popular method for cyber attackers used to deliver malware or steal user’s login credential by encouraging victims to open one malicious attachment or visit a link that will secretly install the malicious payload or steal login user name and password or other sensitive info, which is usually the starting point for further attacks or cyber intrusions. The sender of a phishing email typically poses as a reputable business or known person to get the recipient to click on a link or open an attachment.
Phishing schemes are typically mass mailings to non-specific targets but there are other types of phishing mails that are sent to specific or selected targets, such as spear phishing and whaling (also named CEO fraud). Spear phishing means the cyber attacker might do a little research and find out specific information about the target, from the company website, social media, financial reports, or other public information on the internet, then customize an email, and make it appear more legitimate to the selected specific target. Similarly, whaling is a form of spear phishing aimed at “whales” at the top of the food chain. Whaling targets include the CEO, CFO, and other senior executives and this kind of attack is a big project for cyber attackers as it is planned over a period of time – it could be months before the cyber attacker launches the “last step of attack”. Not surprisingly, the damage caused by whaling is much larger than the loss caused by general phishing email attacks.
In general, phishing mail attacks trigger the below mentioned security risks:
- Leakage of login credentials – many phishing mails lure the victim to log onto a forged (but what appears to be a legitimate) web page to steal the victim’s username and password. The stolen login credential will then be used for another round of attack, such as entering into the mailbox to check historical emails to identify any possible high value target, or logging into the system to steal other sensitive information.
- Financial loss – the attacker might use a sniffer or sniffing attack – gaining access to all the victim’s emails over a long term period to build a full picture of the company’s organization structures and role assignment, plus the status of ongoing projects or business, then forge phishing mails to lure finance staff to transfer money for specific projects or issue financing at the “right” time, such as at the project closing stage. The attacker could also utilize the phishing mail to deliver ransomware to encrypt the user’s data for ransom.
- Reputational damages – the mailbox of the victim can be further used by cyber attackers to send more junk mail or phishing mail to all contacts, including business partners or clients. This would produce much confusion, misunderstanding, embarrassment, and finally cause damage to the company’s reputation, which could further lead to loss of clients. Simply put, such attacks would reduce the confidence of the client to trust a company that fails to protect their customer financial and private information.
What actions can you take to protect your company against phishing mail?
Before figuring out the solutions to combat phishing email attacks, there are several questions that a company should ask of its staff:
- Do employees click on the links or open the attachments in these emails?
- How long does it take your IT team to know if an account has been compromised?
- Do you know which of your employees are more likely to open these types of emails?
The answers to those questions are relevant to the company’s capability to detect the possible security threats and identify the most vulnerable staff to phishing email attacks. The company cannot work out the corresponding solution to prevent or reduce the risks caused by phishing mails without these answers.
Finally, we believe that the below three important actions will help your company increase its data security and protect itself against phishing attacks in China and across Asia.
I. Deploy one email system with advanced security features against insecure emails
The ability to detect and isolate malicious phishing email is a big challenge on both the technical and management side; however, a business-class email service system with embedded advance security features to protect against the phishing mails will be helpful. For example, Microsoft Defender for Office 365 (previously named Office 365 Advanced Threat Protection) can provide an additional layer of protection for email attachments or links inside the mail, via its “safe attachments” and “safe link” features. The Defender will scan the link and determine whether it is safe or not before redirecting the user to the real website once the user clicks the link inside the mail, and blocks the access with alert to the user if it is a known malicious link.
Similarly, the Safe Attachment feature scans the attachment of the email first, and if malware is confirmed, the attachment will be replaced with a notice to the user.
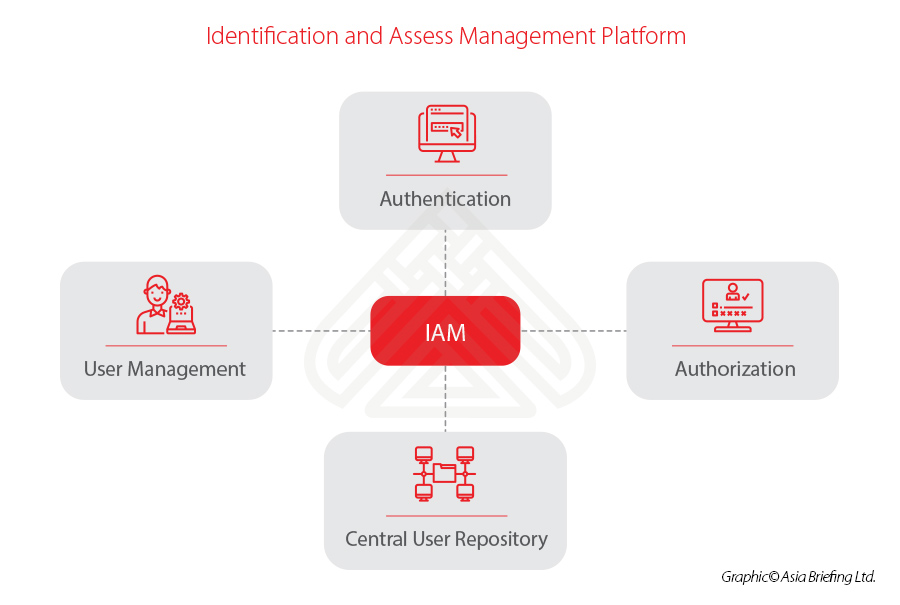
II. Identification and Assess Management (IAM) platform
IAM is a framework of polices and tools used by the IT department to ensure that employees have the appropriate level of access to the company’s assets. The IAM usually includes the following four main features:
As the core components of IAM, multiple factor authentication (MFA) and real-time abnormal logon activity detection are very important and would be the most effective options against phishing email attacks. We provide more details below.
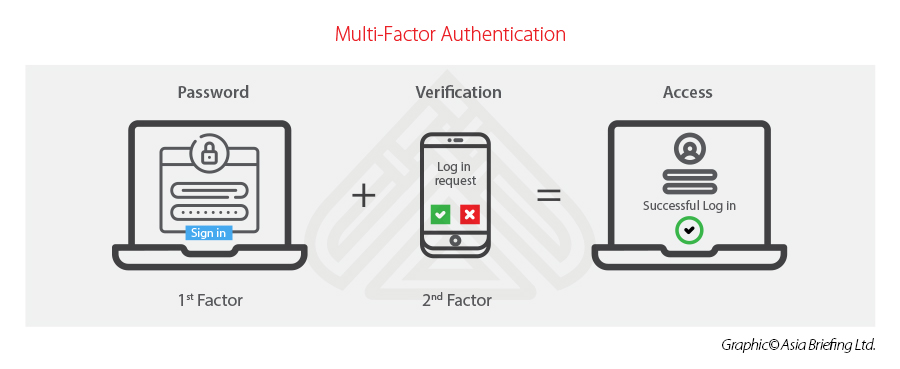
Enable multi-factor authentication for increased identity protection
Most MFA is based on the combination of below three types of information for authentication:
- Things you know – such as the password or PIN;
- Things you have – such as one token or smartphone, which can generate or receive one-time code; and
- Things you are – such as the biometric information like your face, iris, retina, fingerprint, or voice.
Passwords can be easily compromised and one of the main purposes of phishing emails is to steal a user’s login credentials by luring them to log onto a fake website. The deployment of MFA will prevent the attacker from entering a system with a stolen user name and password as their attempt to gain access to a compromised account will be thwarted at the second-factor verification stage.
Get AI to flag suspicious log-on activity within your organization in real-time manner
It is important that your IT team be alerted to suspicious sign-in activity in real-time to respond to a possible cyber security breach ASAP and mitigate security risks. This feature allows the IT staff to track the suspicious activity and alert the original user to reset their password.
AI-based user activity analysis of the IAM platform can evaluate risks based on user log-on locations, IP, device status, accounting status, behavior, and other factors, and then flag any suspicious behavior for your IT team.
For example, the Microsoft 365 platform can ensure the real-time monitoring of all user access activities and AI-based analysis to detect any risky activity and then alert IT staff (such as by sending an email alert showing performance of predefined security control action).
IT admin can further drill down the activity log info and check the activity details to identify the abnormal event, such as the user submitted the correct user name and password but failed to pass the MFA verification from an unusual location:
III. Organize security awareness training for employees and see how “phish-prone” your company really is
Being the end-users for phishing emails, employees are a company’s last line of defense against a security attack.
It is vital that employees receive proper training on how to recognize and react to such emails. Having a good awareness and familiarity with the patterns of phishing emails will enable them to protect their (and your company’s) security. Meanwhile, company should also be able to identify the most vulnerable staff and provide corresponding training in addition to general organization-level training program. One good security awareness training program will be vital for meeting above expectations. As the partner of KnowBe4, we believe its Security Awareness Training Service will bring benefits to increase staff security awareness. KnowBe4 specializes in educating employees about the mechanisms of spam, phishing, malware, etc. and making sure they can apply that knowledge in their daily tasks. Their baseline testing, which sends out sophisticated “fake” phishing emails, enables you to see how “phish-prone” your staff is before any real damage occurs.
About Us
China Briefing is written and produced by Dezan Shira & Associates. The practice assists foreign investors into China and has done so since 1992 through offices in Beijing, Tianjin, Dalian, Qingdao, Shanghai, Hangzhou, Ningbo, Suzhou, Guangzhou, Dongguan, Zhongshan, Shenzhen, and Hong Kong. Please contact the firm for assistance in China at china@dezshira.com.
We also maintain offices assisting foreign investors in Vietnam, Indonesia, Singapore, The Philippines, Malaysia, Thailand, United States, and Italy, in addition to our practices in India and Russia and our trade research facilities along the Belt & Road Initiative.
- Previous Article RCEP FTA unterzeichnet: Was können ausländische Investoren von China erwarten?
- Next Article China’s Patent Law Reviewed: Five Major Amendments